Most access-related risks don't appear overnight.
They form slowly, through a series of reasonable decisions made under pressure. A permission is expanded to resolve an incident. A temporary role is added to unblock work. An exception is granted with the intention of revisiting it later.
Individually, none of these changes are reckless. Collectively, they can reshape access in ways teams don't fully notice until much later.
By the time a security review happens, the environment isn't necessarily unsafe — it's unclear.
Why Access Risk Hides in Timelines, Not Policies
Security teams are usually very good at understanding the current state.
They know who has access today.
They know which roles exist.
They know what policies are active.
What's harder to see is how access evolved to reach that state.
Most tools present access as a snapshot. A list of permissions, roles, and identities frozen in time. That's useful — but incomplete.
Risk doesn't live in the snapshot.
It lives in the sequence of change.
A role that looks acceptable today may have grown quietly over months.
An exception that made sense during an outage may never have been removed.
Access that was temporary may have become permanent through drift.
Without seeing that progression, teams are left guessing.
The Limits of Logs and Static Views
Logs can show when something happened.
Policies can show what exists now.
But neither explains why access changed, or how one adjustment led to another.
Security teams often end up reconstructing history manually:
comparing timestamps across tools
reviewing tickets and approvals
asking engineers to remember decisions made months ago
This process is slow, incomplete, and stressful — especially during audits.
The problem isn't a lack of data.
It's a lack of coherent narrative.
How Risky Drift Forms Quietly
Access drift rarely comes from malicious intent.
It comes from urgency.
During incidents, speed matters more than documentation. During growth, automation accelerates change faster than context can be preserved. Over time, the original intent behind access decisions fades.
What remains is configuration without explanation.
This is why risky access often surfaces late — during audits, investigations, or incidents — when fixing it is more costly and disruptive.
Seeing Access as a Timeline, Not a Snapshot
To surface risky drift early, teams need to see access differently.
Not as a static list — but as a timeline.
A visual access timeline shows:
when access was granted
how permissions expanded or contracted
which changes were meant to be temporary
where drift accumulated quietly
This shifts security reviews from reactive to proactive.
Instead of asking, "Is this access acceptable right now?"
Teams can ask, "When did this change — and does it still make sense?"
That difference is critical.
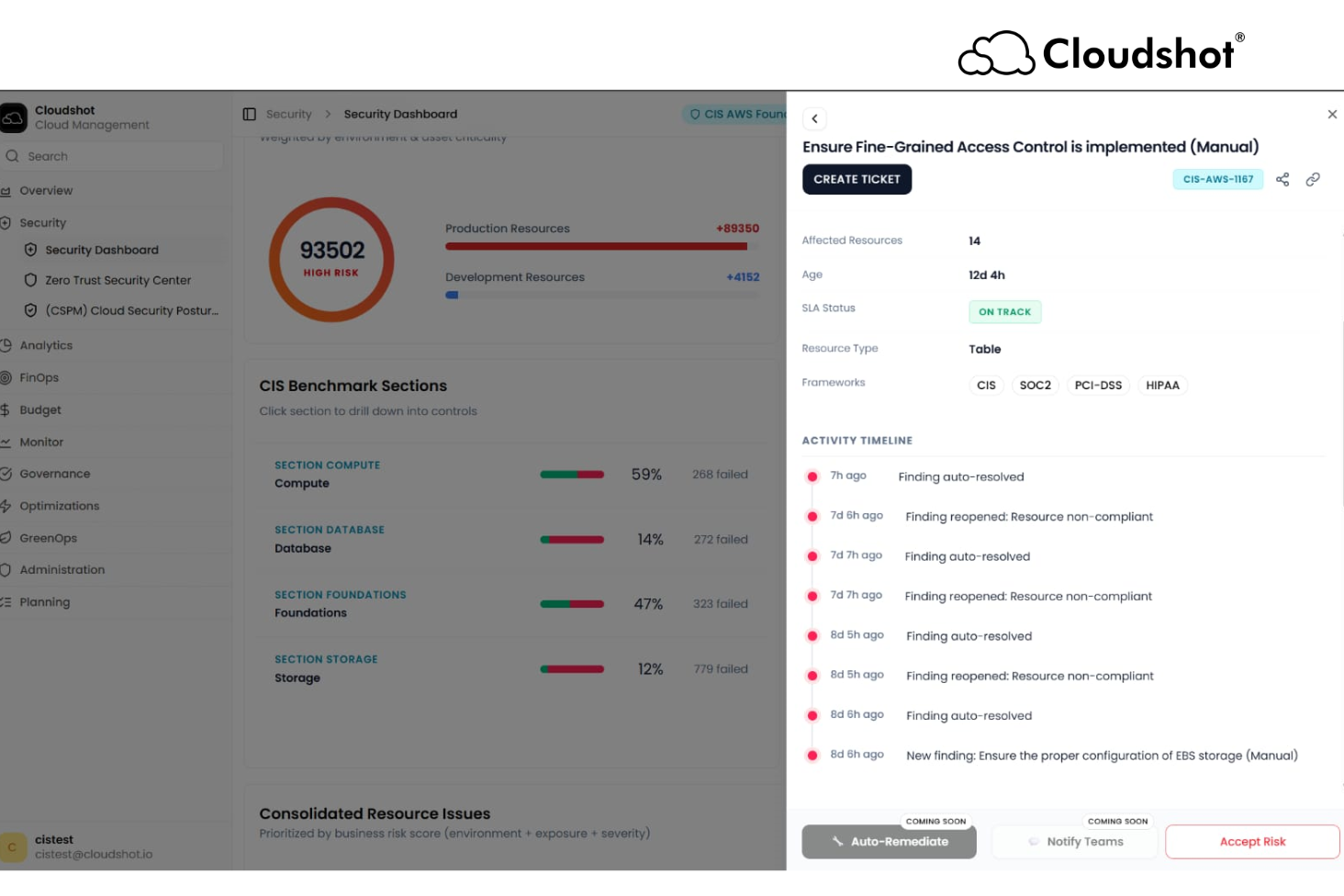
How Cloudshot Enables Early Clarity
Cloudshot turns access changes into a visual timeline that Security and Architecture teams can review together.
Instead of hunting through logs or stitching context across tools, teams see a shared view of how access evolved — aligned with infrastructure changes and system behavior.
This clarity allows teams to:
identify risky drift before audits
remove outdated access confidently
explain decisions clearly during reviews
Security reviews stop feeling like investigations. They become confirmations.
From Audit Anxiety to Audit Readiness
When access history is visible, teams no longer rely on memory or assumption.
They can explain why access exists.
They can fix drift early.
They can prepare for reviews without last-minute stress.
This is how compliance becomes routine — not reactive.
Because access risk doesn't start with policy violations.
It starts with changes no one noticed accumulating.